the maze
The Maze#
The Maze - GOTY edition
This fabulous “Game Of The Year” edition contains all the levels, characters and
DLCs of the acclaimed game “The Maze”.
“The Maze” is a text-based game where you play as Ampersand, the iconic hero
that should avoid all the monsters (that’s easy, actually: there are none) and
find the precious treasure.
Of course, as a CTF player, you don’t really care about the treasure, do you?
Yes, you want a flag, that’s clear.
There are no flags in the maze, though.
You should probably find a way to escape…
MD5:
07785b37292c80ee1de683913fb43384 the_maze
This is a remote challenge, you can connect to the service with:
nc maze.challs.cyberchallenge.it 9404
Download binary: the_maze
Solution#
+-+
|&| <--- Start
| |
| +-----------------------------+
| X X X |
| XXXXXXX X XXXXX X X X XXX XXXX|
| X X X X X X |
| XXXXX X X XXX XXXXX X X X X XX|
| X X X X X X X X |
| XXX XXXXX XXXXXXXXXXXXXXXXX XX|
| X X X X |
|XX X XXX XXXXX X XXX X X XXXXX |
| X X X X X X |
|XXXXXX XXX X X X XXX XXXXXXXXXX|
| X X X X X X |
| XXX X XXXXXXXXX XXX XXX XXX X |
| X X X X X X X |
|XX X X X XXX XXXXXXXXX X XXXXX +----------+
| X X X X X X Treasure |
+------------------------------------------+
This challenge is a maze game, you have to go from the start to the treasure to
win, but we care about the flag, so I started reading the decompiled code and I
easily spotted a system("cat flag.txt").
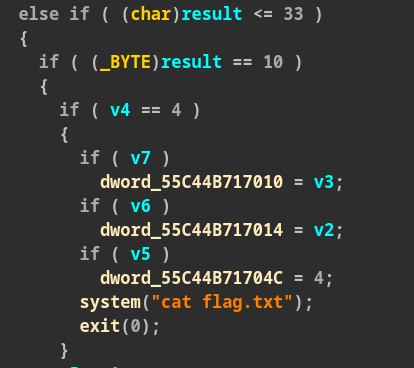
I checked if there was a buffer overflow, and there is a fgets which writes 4096 bytes on a small buffer, but we can’t use it to control the execution. Besides, checksec showed:
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
FORTIFY: Enabled
so we couldn’t overwrite the return address anyway without bypassing the canary, which we can’t leak.
The next thing I checked was if we could manage to execute system("cat flag.txt"),
and the only way this is possible is by playing the game and passing all the
checks until that instruction.
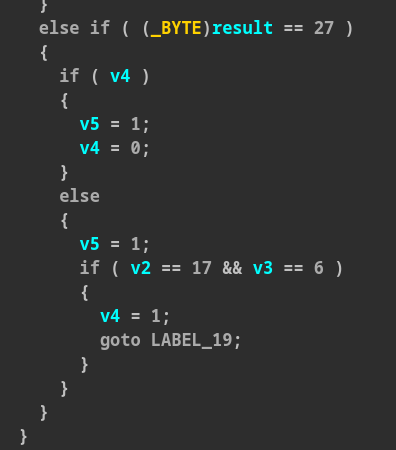
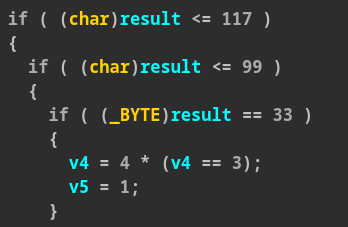
The most difficult check is v4==4, and to pass
it we have to go right 16 times (to set v2 to 17) and down 5 times (to set v3 to
6), but some movements are blocked by the walls and the only combination
possible is: “ddd”+“r”*16+“dd”.
After understanding this we simply have to increment v4 from 1 to 4, and some
checks specifically do this:
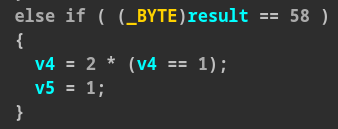
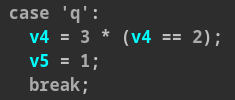
After doing so we simply send a newline (0x10) and the binary will print us the flag.