eliza
Remote: eliza.challs.cyberchallenge.it,9131
Download binary: eliza
Solution
First we check the security settings of the binary with checksec from pwntools:
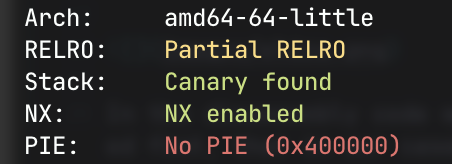
The executable is position dependent (No PIE), so if we can manage to overwrite the return address in the stack, we can execute any function we want of the program. So now we just need to see if the process has any buffer overflow we can exploit and it’s done! right? Well, no. The executable has a canary which impedes us to use any buffer overflow to overwrite the return address without overwriting it as well, triggering the security mechanism that will stop the execution if the canary has been modified.